One of the victims of Eticosearch.com “ my computer runs abnormally recently, and my browser does not work properly, too. What’s wrong with my computer? Am I infected with any virus?” Wow, if you are meeting such problem, and you are eager to know how to stop it, I recommend this post to you!
>>> How to remove Eticosearch.com completely?
What is Eticosearch.com?
Eticosearch.com regards itself as a helpful and standard website which is able to enrich Internet user’s regularly browsing experience by providing a search engine called All in One Search Engine that is similar as Yahoo, Google, Firefox or Bing. However, Eticosearch.com is not as what it has claimed. In reality, it is categorized as a browser hijacker which does no good to the computer but does harm to your system by triggering many malicious activities on your computer. Once finding Eticosearch.com running on your system, you should take effective methods to remove it from your computer completely.
What Does Eticosearch.com Do to Your System?
1.Eticosearch.com gets access to your computer without your notice or permission.
2.Eticosearch.com will redirect your browser to other deceptive websites and change your default search engine to Eticosearch.com.
3.Eticosearch.com makes many other infections attack your computer.
4.Eticosearch.com keeps track of your online activities and then send those collected confidential information to the third party.
How Can I Get Eticosearch.com?
1.Download and install free software bundled with Eticosearch.com from the Internet.
2.Check the spam email attachments.
3.Browse some websites which have been hacked by cyber criminals.
What Can I Do to Remove Eticosearch.com Completely from the Infected System?
Eticosearch.com does not good to your computer, the longer it stays on your computer, the more harms it will do to your system. Once noticing Eticosearch.com is running on your computer, take the following methods to remove it quickly.
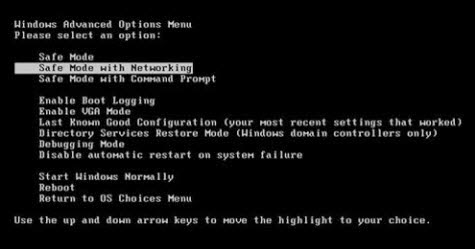
Method one: remove Eticosearch.com manually step by step.
Step one: Delete Eticosearch.com from browsers.
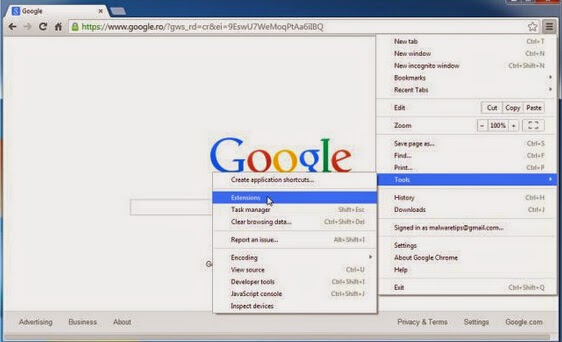
1.Restore on Google Chrome
1) Tap Alt+F and the select Settings.
2) Then check Show home page button and select Change.
3) Remove the website provider by the hijacker and enter a new one.
2. Restore on Mozilla Firefox
1) Tap Alt+T and select Options.
2) Select General tab.
3) Then remove the unwanted address and enter a new one → click OK.
3. Restore on Internet Explorer.
1) Tap Alt+T and select Internet Options.
2) Select General tab.
3) Remove the undesirable website address and enter a website of your choice → click OK.
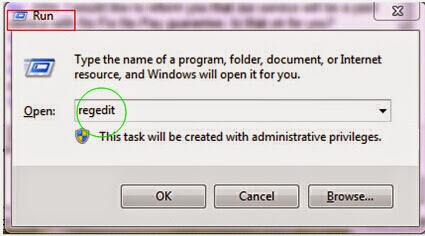
Step two: Remove all the registry entries by using the following processes.
1) Open Registry Editor by clicking Windows+R keys together.
2) Figure out all malicious registry entries as follows and delete them:
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\run\random
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |Regedit32
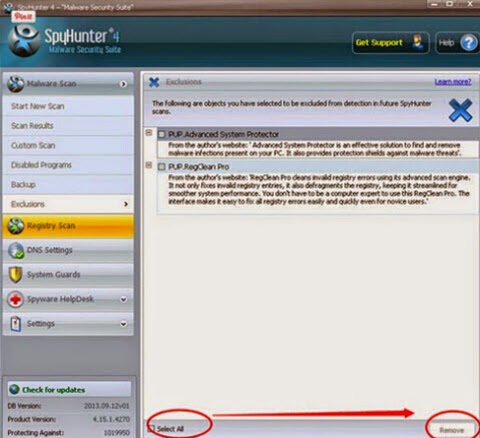
Method two: automatically block Eticosearch.com effectively with SpyHunter.
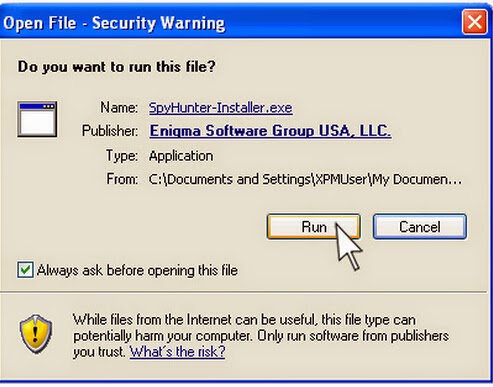
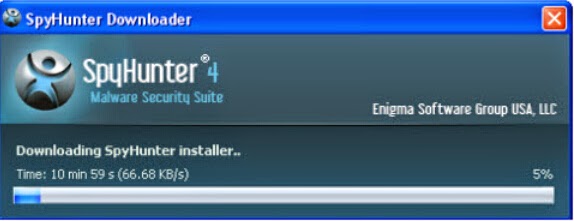
Step one: Click on the icon below to download SpyHunter automatically.
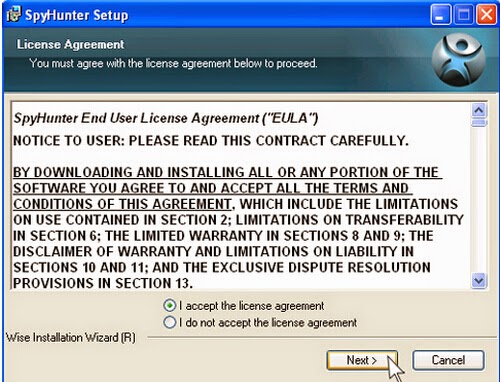
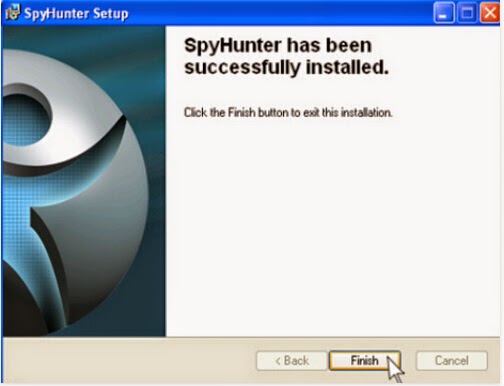
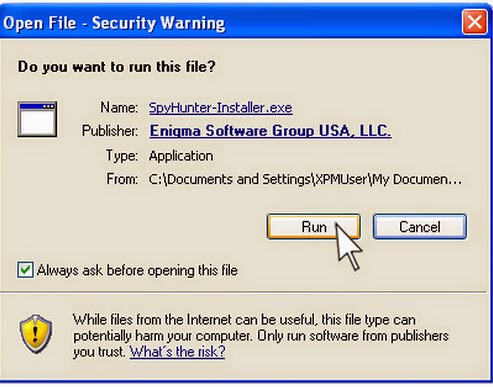
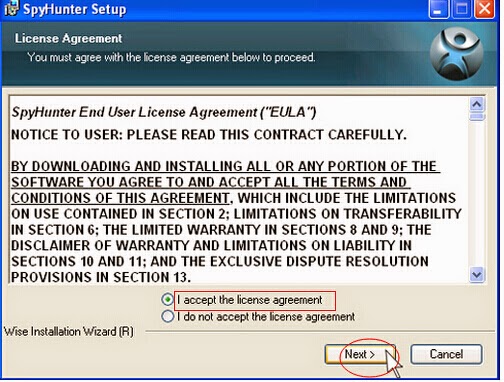
Step two: Follow the instructions to install SpyHunter on your computer step by step.
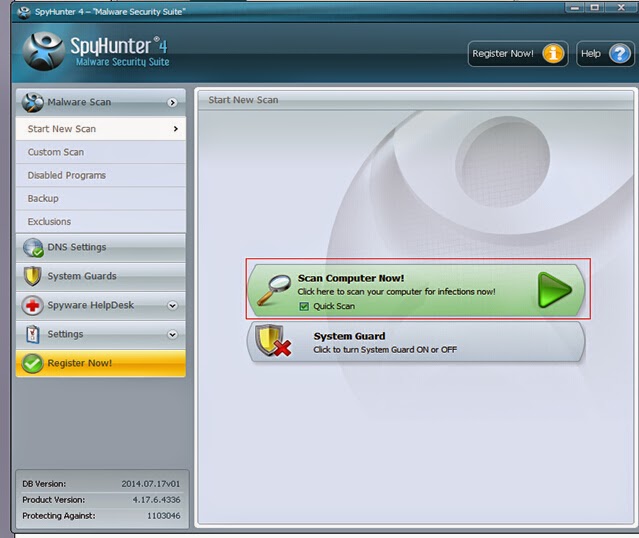
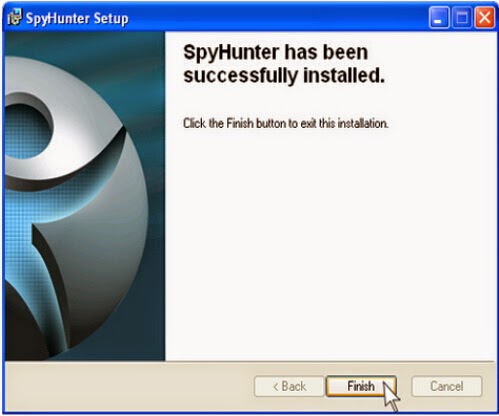
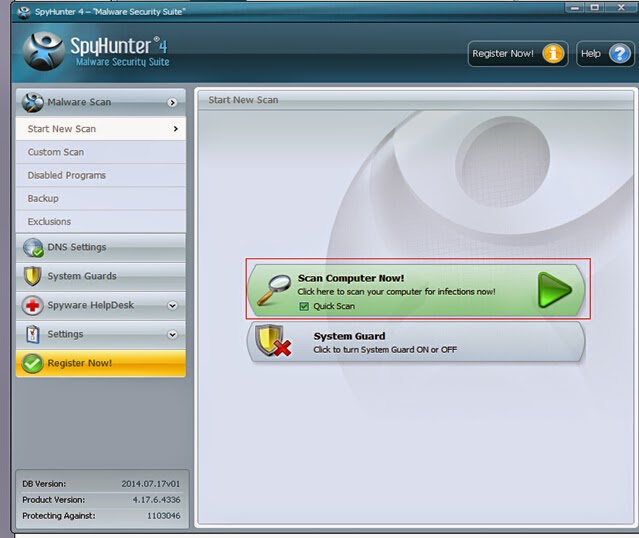
Step three: After finishing the installation, run SpyHunter and click "Malware Scan" button to scan your computer, and then clean up files and entries related to Eticosearch.com completely.
Step four: Restart your computer to check whether your computer works properly again.
Attention: It is quite complicated to remove Eticosearch.com manually, so for the safety of the computer, I
strongly recommend SpyHunter to you. As a kind of powerful anti-virus program, SpyHunter can terminate Eticosearch.com completely, can take effective measures to protect your system in the future as well.



DPAN8PE%7BM%244T1SKD.jpg)


.png)






6MX6MC%40L%24V4G6A2G%7B%7BY%7DB.jpg)
%60F%5BTO8OHM.jpg)
2(9%24P%3EI%60%5DAB.jpg)
J%5DZJ(CR%7DZ%7DW.jpg)